Understanding Card Testing Fraud Attacks and How to Stop It

Chargebacks?
No longer your problem.
Recover 4x more chargebacks and prevent up to 90% of incoming ones, powered by AI and a global network of 15,000 merchants.
Card testing is a silent prelude to bigger attacks. They're reconnaissance missions for the $500 purchases that'll drop on your chargeback ratio six months from now. The brands winning this fight treat card testing prevention as the first line of chargeback fraud prevention. Not a separate problem to solve. If you're not doing that, you should start today.
Card testing fraud is one of the most dangerous threats you barely notice. It usually starts small. A few bucks here and there. Easy to dismiss. Easy to write off as the "cost of doing business online."
That's the trap.
Every one of these micro-transactions is a probe. When a charge goes through, fraudsters know they've got a live card. AND the green light to exploit it at full throttle. By the time you catch on, the carnage is already in motion.
Here’s the part that stings. Even if they never run the cards elsewhere, you still lose. Those tiny, insignificant charges often metastasize into more expenses. We're talking chargeback fees, customer frustration, processor penalties, and reputational damage.
The good news? You can catch these attacks and shut them down before they cost you money once you know what to look for.
How Card Testing Fraud Works and Signs of Card Attacks
Card testing fraud is a validation scheme where fraudsters and cybercriminals make small, low-risk transactions to verify whether stolen, purchased, or AI-generated credit card numbers are active, without alerting the cardholder or triggering the merchant's fraud systems.
Card testing fraud follows a predictable methodology. Cybercriminals have refined this strategy into an efficient operation.
Step 1: Data Acquisition
The criminal obtains credit card information. To achieve this, they often orchestrate a major data breach, exposing millions of card details at once. Some fraudsters use sophisticated phishing campaigns to trick consumers into surrendering their payment information. Underground marketplaces also sell compromised card data (for as low as $5 for a set of card details).
Stripe says card testing is a high-impact form of cybercrime affecting merchants, financial institutions, and consumers worldwide.
Step 2: Validation Through Micro-Transactions
Once they obtain the stolen card data, the attackers launch systematic validation campaigns. They deliberately choose low-dollar amounts below most fraud detection thresholds.
Step 3: Active Card Identification
The validation process reveals which cards remain functional and uncompromised. Attackers particularly value cards that process without requiring additional verification. No restrictions equals easier targets for future exploitation.
Step 4: Monetization of Verified Cards
Attackers either exploit the cards directly through larger fraudulent transactions or sell the verified information at premium prices.
The digital nature of card fraud allows criminals to operate remotely and at scale. Law enforcement prosecution, even when detected, is often challenging.
The Scale and Impacts of Card Testing Attacks
Card testing isn't just widespread. It's a high-volume, automated assault on the payments ecosystem.
For instance, payment giant Stripe documented blocking over 20 million card testing attempts daily during peak attack periods in 2022. There were 269 million card records posted on the dark and clear web in 2024.
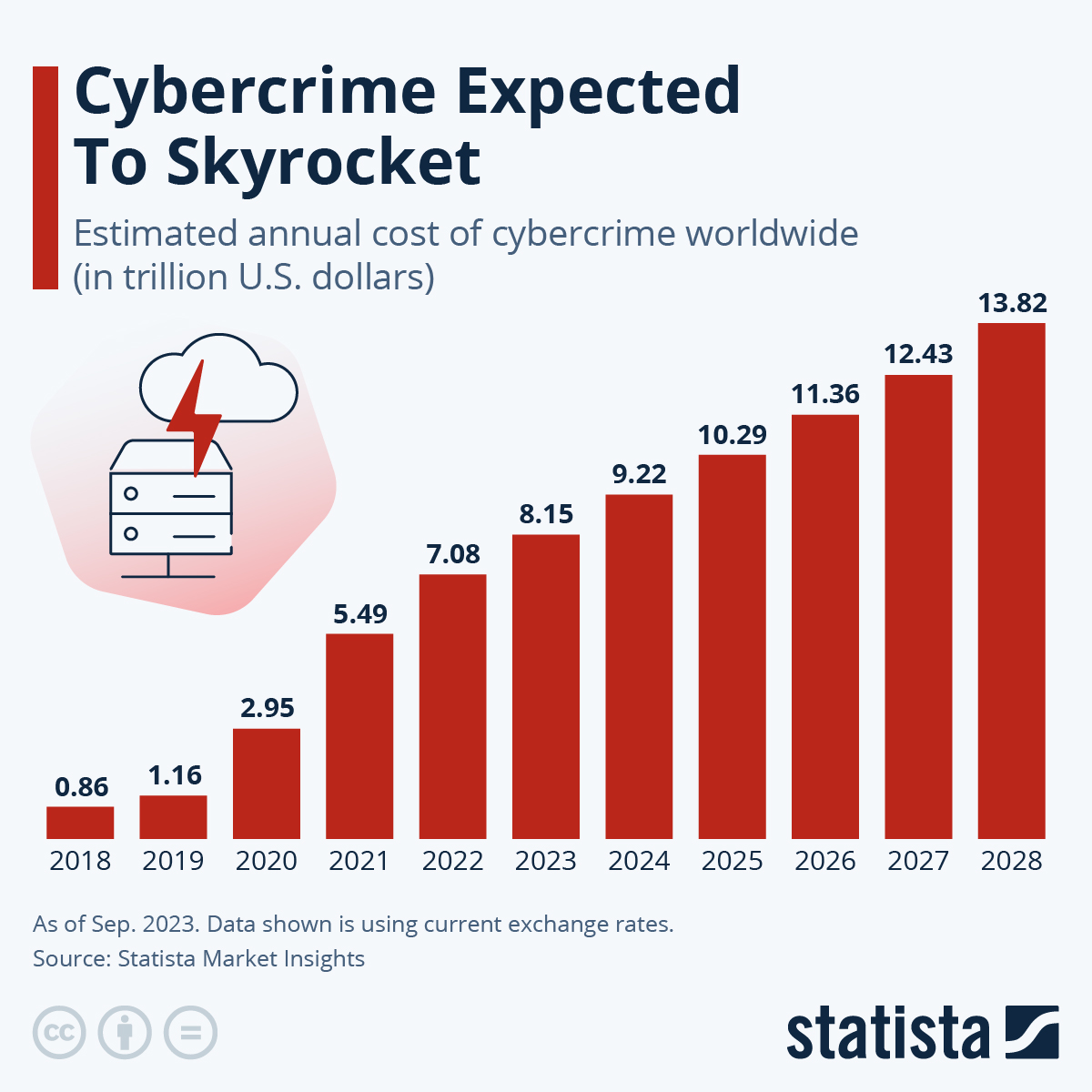
Impacts of Card Testing Attacks on Businesses
Every time a merchant falls victim to a card testing attack, they get pummeled from three directions:
- Direct Financial Losses: Those "harmless" charges quickly become significant chargeback fees ($15 to $100, irrespective of transaction size). Our chargeback statistics indicate that U.S. merchants lose at least $4.61 for every $1 of fraud once you factor in transaction fees, penalties, and operational costs. At scale, card testing can quietly wipe off millions annually.
- Processor Scrutiny: Rising fraud ratios trigger payment processors to flag merchants as high-risk. Under Visa's new VAMP guidelines (effective October 2025), Visa will flag merchants with over 300,000 enumeration attempts per month as "Excessive".
- Operational Drain: Policy changes like VAMP keep fraud teams on high alert. From chasing sudden transaction spikes to handling customer complaints over mystery charges, bot-driven traffic drains merchants' resources. For smaller businesses without a dedicated fraud team, these costs can be overwhelming.
Besides reshaping a merchant's margins, reputation, and ability to operate, card testing fraud also affects customers.
Impacts of Card Testing Attacks on Cardholders
For consumers, card testing creates a chain reaction of stress and vulnerability.
- Unauthorized Charges: Many cardholders first notice fraud through random micro-charges from unfamiliar merchants. While banks typically refund them when disputed, the hassle of reporting, waiting, and replacing cards erodes trust.
- Data Resale and Escalation: As highlighted earlier, a successful test confirms that the stolen card data (number, CVV, expiration, and billing address) is valid. That card profile then becomes prime inventory on dark web marketplaces. It sets the stage for large-dollar fraud, account takeover, or identity theft.
- Long-Term Consequences: In severe cases where fraud extends beyond card testing, victims discover downstream impact, including credit score impairment, loan denials, or identity misuse. That takes months or even years to resolve.
Even after being reimbursed, customers report heightened anxiety, abandoned online purchases, and reduced trust in digital transactions due to card testing fraud.
Impacts of Card Testing Attacks on the Broader Ecosystem
Card testing doesn't just hurt merchants and cardholders. It creates systemic vulnerabilities across the digital payments infrastructure.
Payment Processors and Financial Institutions Under Pressure
Banks and processors spend billions fighting fraud. JPMorgan Chase alone invests $15 billion annually in fraud prevention technology. They earmark billions for cybersecurity and card testing prevention.
With millions of disputes to resolve, these institutions push costs downstream to merchants through higher fees and stricter compliance rules.
Erosion of Consumer Trust
Fraud concerns drive behavior: 25% of shoppers abandon online purchases due to security concerns. Rising chargebacks further undermine confidence. It forces businesses to spend heavily on customer retention.
Regulatory Burden
Fraud spikes prompt tougher regulations, such as PSD2, PCI DSS 4.0, VDMP, which can cost large merchants millions annually in compliance. Smaller businesses often struggle to keep up, risking fines or even restricted payment access.
The high cost of fraud prevention squeezes out smaller processors and reduces merchant choice. The result? Higher transaction fees and less competition across the eCommerce economy.
Common Targets of Card Testing Fraud
Card testers don't shoot blind. No. They focus on sectors that enable two key aspects:
- High transaction volume
- Expedited approval processes.
The former helps them blend into the noise. The latter ensures automated testing sprees go uninhibited.
With that in mind, below are common targets of card testing scams:
eCommerce Sites
Online retailers often process thousands of transactions daily. Most customers expect lightning-speed checkouts. And fraudsters know it. They'll unleash bots that can cycle through 10,000 stolen card numbers in under 1 hour. These low-value transactions will look completely normal in your transaction logs. By the time you notice the pattern, they've already validated hundreds of working cards and moved on to drain them elsewhere.
Subscription Services
Monthly subscription services are a fraudster's dream scenario. That $9.99 Netflix-style charge? It's perfect for testing cards. It's recurring. It’s predictable. Cardholders barely glance at these charges on their statements.
Streaming platforms and SaaS providers report that card testing now accounts for an estimated 20-25% of their declined transactions. Said another way: For every legitimate transaction declined, your fraud prevention system likely catches three to four card testing attempts.
Donation Platforms
Charitable sites face a cruel irony. The same trust and goodwill that drives donations makes them even more vulnerable to fraud. Small donation amounts ($1-$5) are standard and expected. That makes it nearly impossible to distinguish between a genuine $3 donation and a $3 card test. Worse, nonprofits often operate with limited fraud prevention budgets. They’re easy targets that fraudsters exploit ruthlessly.
Event Ticketing Platforms
Local events, lotteries, and small venue tickets typically process fast approvals for low-dollar purchases. That $8 raffle ticket or $25 community theater seat gets approved instantly. No questions asked. Fraudsters know this. They use these platforms as testing grounds before moving on to bigger targets.
Mobile Apps
In-app purchases are fraud nests, which lead to App Store chargebacks. Those $0.99 game upgrades and $2.99 premium features process so quickly that fraudsters can validate entire batches of stolen cards in minutes. App stores and gaming platforms see some of the highest card testing volumes. Why? Because the friction is so low. And the amounts are so trivial. Nobody pays attention until it's too late.
The pattern is clear. If your business model depends on quick approvals for small amounts, you're on card testers' radar. The question isn't whether they'll target you. It's whether you'll be ready when they come knocking.
Here’s what to look for in potential card testing scams.
Notable Card Testing Attack Indicators
The primary warning signs that indicate your business may be under a card testing attack are as follows:
- Transaction Pattern Anomalies: Watch for unusual clustering of small-value purchases within short timeframes. Legitimate customers rarely make multiple micro transactions consecutively. Furthermore, these attacks often occur during seasonal peaks, such as Black Friday, Cyber Monday, and holiday sales periods, when monitoring may be less intensive.
- Multi-Card Testing from Single Sources: Monitor for attempts using different card numbers originating from identical IP addresses, devices, or browser fingerprints. This behavior is almost always proof-positive of automated testing tools cycling through stolen card databases.
- Elevated Decline Rates: Sudden spikes in transaction failures are often a sign of card testing. Criminals usually work with partially corrupted data sets. This leads to abnormal rejection rates as they attempt to validate expired or compromised cards.
- Geographic and Behavioral Inconsistencies: Flag transactions where billing addresses don't match IP locations, or where customer behavior deviates significantly from normal patterns. Attackers can use proxy servers and VPNs to mask their locations.
- Velocity-Based Red Flags: Rapid-fire transaction attempts, especially those testing different payment amounts or card details in quick succession, signal automated testing rather than genuine customer behavior.
So how do you stop the madness? Let's examine proven card testing prevention strategies you can apply as you prepare for the forthcoming BFCM season.
Counterintuitive Steps to Prevent Card Testing Fraud
Here's the thing. Instead of just defending against card testing, what if you made your site such a pain in the butt for fraudsters that they'd rather move on to easier targets?
Sure, you can! Here’s how:
Step 1: Intentional Friction for Micro Transactions
Most merchants obsess over creating frictionless checkouts. And for a good reason. Extra steps at checkout often drive cart abandonment.
But there's a flip side. Card testers exploit seamless flows. That's why adding smart guardrails is critical. Even adding small friction points, such as requiring a ZIP code match, for transactions under $10 can disrupt automated testing.
And it doesn’t meaningfully affect legitimate customers. Research shows that friction upon entry optimizes value. Adding good friction in your CRO process make you more money. It increases your cost per action: your show rates, close rates, and cash collected will increase.
Step 2: The Honeypot Trap
Savvy merchants create fake "express checkout" options that look appealing to bots but trigger immediate blocks. Card testers gravitate toward anything that promises faster processing. Smart moves like this make it easy to track and ban perps.
Step 3: Geographic Fencing That Makes Sense
Instead of blanket country blocks, successful merchants pinpoint their actual customer geography and create smart fences. If you've never had a legitimate customer from region X, why process payments from there at 3 AM?
Step 4: The "Failed Payment Redirect" Strategy
When payments fail, most merchants just show an error page. That doesn’t do much to stop fraud. Quick, clean payment failure response lets fraudsters test the next card immediately. Advanced fraud fighters have stepped away from such a rudimentary strategy.
They redirect failed attempts to slightly complex verification processes. That turns each payment failure into annoyingly more work for fraudsters while legitimate customers get helpful support.
Step 5: Supplier Network Intelligence
The merchants' winning card testing fights share attack patterns with their payment processors, shopping cart providers, and even competitors. When fraudsters strike one Shopify store with a new technique, smart merchants get alerts before the same attack strikes them.
Step 6: Transaction Timing Warfare
Card testers work in predictable patterns. Off-hours, peak period, sessions with fewer human monitoring...those are their MO. Some merchants deliberately show down or add extra verification during high-risk windows (like 2-6 AM) when legitimate customers are rare anyway.
The question isn't "what's industry standard?" It's "what makes this particular business unprofitable for fraudsters to target?"
These strategies work because they think like attackers. Not like compliance officers. They know that $2 card tests become $100 chargeback fees.
Why Card Testing Prevention is Chargeback Prevention in Disguise
Card testing is a silent prelude to bigger attacks. They're reconnaissance missions for the $500 purchases that'll drop on your chargeback ratio six months from now.
Each card maxed out after a successful validation is a crisis waiting to happen. And guess where cardholders come looking when they discover those charges? The last merchant who "proved" the card worked.
Turn Prevention Into Profit Protection Today
Intelligent chargeback prevention starts way before the dispute. When you block card testing, you're not just stopping small transactions. You're preventing the fraud ecosystem that creates future chargeback headaches. Every bot blocked today saves you money in chargeback fees tomorrow.
That's why sophisticated merchants integrate automated chargeback management as an integral aspect of card testing prevention.
Here is a clear explanation of how that works in two phases:
Phase 1: Pre-Chargeback Alert
When a cardholder detects the bill and disputes it with their card issuer, the system sends an advanced alert to you. You can then take the most prudent decision: auto-refund or escalate evidence compilation and dispute filing (if the case is winnable).
Phase 2: Block and Blacklist
When a chargeback comes in tagged as "card testing fraud," your system automatically updates blocking rules to catch similar patterns in real-time.
Potential chargeback losses become intelligence that makes future attacks more expensive for fraudsters.
ROI That Makes Sense
A comprehensive chargeback prevention technology, like Chargeflow, pays for itself. When you calculate voided chargebacks, not just blocked transactions, the math makes sense.
Block 1,000 card test today, prevent 100 successful validations, and avoid 50 downstream fraud incidents. That's potentially $2,500 in chargeback fees you never have to fight.
In closing this article, I leave you with a final thought. The brands winning this fight treat card testing prevention as the first line of chargeback fraud prevention. Not a separate problem to solve. If you're not doing that, you should start today.

Chargebacks?
No longer your problem.
Recover 4x more chargebacks and prevent up to 90% of incoming ones, powered by AI and a global network of 15,000 merchants.













































.png)








